What Is 23 NYCRR 500?
The New York Department of Financial Services (NYDFS) maintains cybersecurity requirements for financial services institutions located or doing business in New York via Part 500 of Title 23 of the Official Compilation of Codes, Rules and Regulations of the State of New York (23 NYCRR 500). Covered entities are required to establish cybersecurity programs, identify cybersecurity leaders within the organization, assess risks, and develop plans to address these risks.
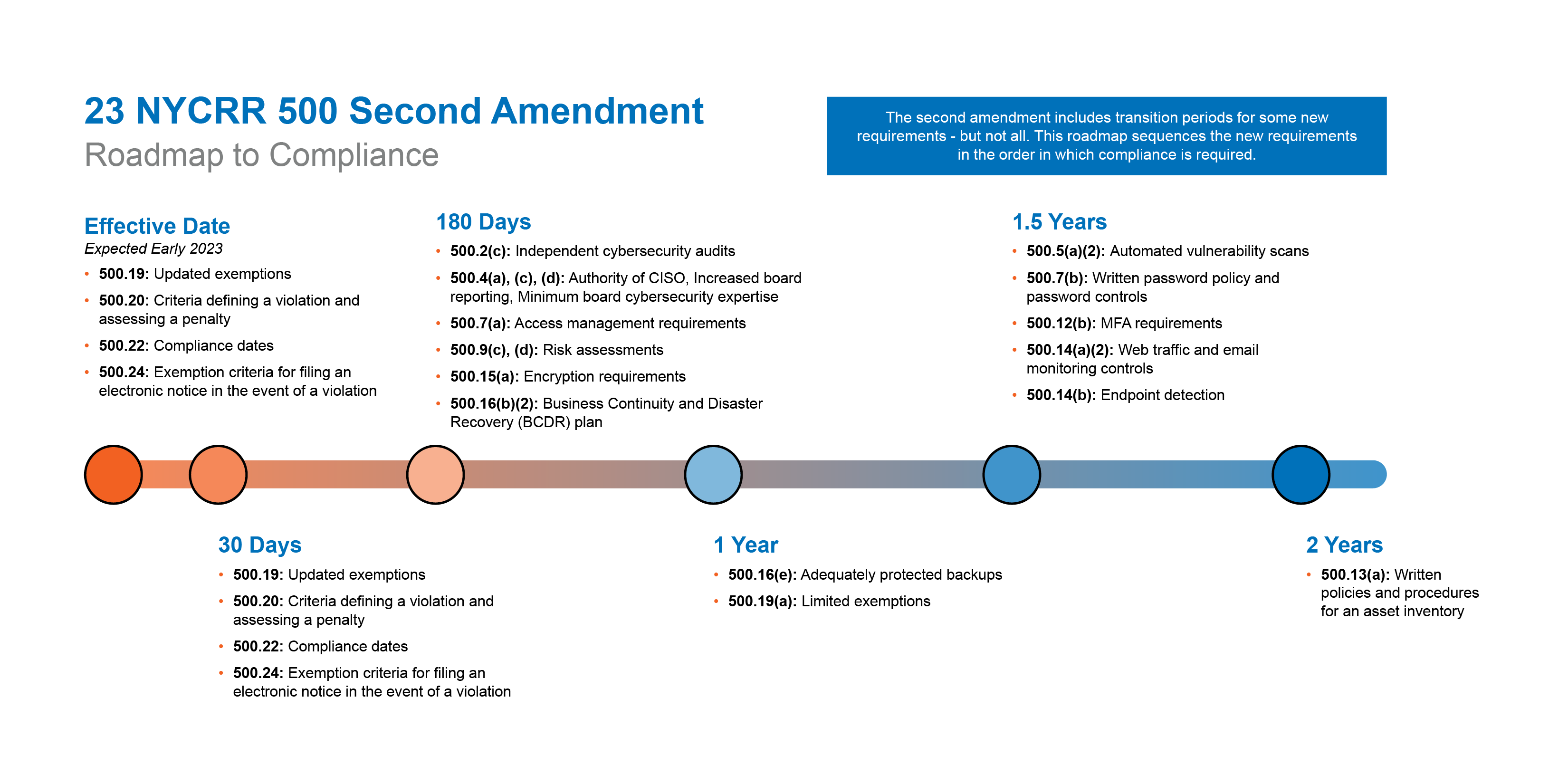
A second amendment was published on November 9, 2022, for a 60-day comment period. It will likely go into effect in early 2023, with a compliance deadline of 180 days from the effective date for most requirements.
Does 23 NYCRR 500 Apply to You?
If your company operates under the Banking Law, the Insurance Law, or the Financial Services Law, 23 NYCRR 500 applies. The second amendment clarifies that this is regardless of whether your company is also regulated by other government agencies, and provides the following updates to limited exemptions for covered entities that have:
- Fewer than 20 employees and contractors of the covered entity and its affiliates.
- Less than $5M in gross annual revenue in each of the last 3 fiscal years.
- Less than $15M in year-end total assets.
What Are the Major Changes?
- New specific requirements for Class A companies, including periodic independent audits and risk assessments performed by external experts.
- Increased cybersecurity governance through more frequent board reporting and demonstrated cybersecurity expertise on the Board.
- Stringent and time-bound notification requirements defined for data breaches and other cybersecurity events.
- New or increased scope for security safeguards, including penetration testing, email and web filtering, encryption, and multi-factor authentication.
What Are the Risks of Non-Compliance?
Financial
Fines up to $6M have historically been levied by NYDFS for cybersecurity.
Reputational
Public release of NYDFS enforcement action could harm brand image and put client relationships at risk.
Regulatory
Increased scrutiny in annual NYDFS examinations and added pressure of ongoing investigations and monitoring.
Security
Potential gaps in common-sense, industry-standard security controls, leading to increased risk of breach or personal data misuse.
Class A Companies and Specific Requirements
The draft amendments create a new distinction, “Class A companies,” defined as covered entities with at least $20,000,000 in gross annual revenue in each of the last two fiscal years from business operations of the covered entity and its affiliates in NY and:
- More than 2,000 employees, including those of both the covered entity and all its affiliates no matter where located, or,
- More than $1,000,000,000 in gross annual revenue average over the last three fiscal years from all business operations of the covered entity and all its affiliates.
Under these draft amendments, Class A companies will have five additional requirements:
Independent cybersecurity audits (§§500.1(f), 500.2(c))
Class A companies will be required to conduct independent audits of their cybersecurity programs at least annually. These audits must be conducted by external auditors who are free to make their own decisions and are not influenced by the covered entity being audited or by its owners, managers, or its employees.
Risk assessments (§§500.1(n), 500.9(c),(d))
All covered entities will be required to complete risk assessments at least annually, or when a change in business or technology causes a material change to the covered entity’s cybersecurity risk. Class A companies will be further required to utilize external experts and conduct a risk assessment at least once every three years.
Passwords to monitor privileged access (§500.7(b))
Class A companies will be required to monitor privileged access activity and shall implement password vaulting solutions for privileged accounts that meet industry standards and an automated method for blocking commonly used passwords, or another CISO-approved equivalent security access control.
Implementation of endpoint detection and response solutions (§500.14(b))
Class A companies will be required to implement an endpoint detection and response solution to monitor anomalous activity, including but not limited to lateral movement, and a solution that centralizes logging and security event altering, or reasonably equivalent, CISO-approved secure controls.
Cybersecurity Governance
Part 500 provides specific requirements for written policies, the appointment of a CISO, and cybersecurity reporting to the board of directors. The draft amendments ensure the CISO has adequate authority, the board is knowledgeable and informed, policies are maintained and updated, and the covered entity’s business is resilient.
Authority of CISO (§500.4(a))
The role of the CISO remains largely unchanged. Each covered entity must designate a qualified CISO who is responsible for overseeing and implementing the entity’s cybersecurity program. Under these amendments, the covered entity must ensure that the CISO maintains adequate authority to ensure cybersecurity risks are appropriately managed, including the ability to direct sufficient resources to implement and maintain a cybersecurity program.
Increased board reporting (§500.4(c))
CISOs will be required to provide annual reports to the board on the confidentiality of nonpublic information and integrity and security of systems, existing policies and procedures, material cybersecurity risks, the effectiveness of the cybersecurity program, material cybersecurity events involving the covered entity, and plans for remediating material inadequacies. The CISO will also need to provide timely reporting to the board of any material cybersecurity issues that occur between these annual updates.
Minimum board cybersecurity expertise (§500.4(d))
The board members will be required to maintain sufficient expertise and knowledge or be advised by persons with sufficient expertise or knowledge, to effectively oversee cybersecurity risk management.
Annual policy approval (§500.3)
The board will be required to approve the entity’s cybersecurity policies at least annually.
New requirements for Business Continuity and Disaster Recovery (BCDR) plan (§500.16(b)(2))
In addition to an incident response plan, under the draft amendments, covered entities will be required to maintain and test a Business Continuity and Disaster Recovery (BCDR) Plan. This BCDR Plan shall be designed to ensure the availability and functionality of the covered entity’s services and protect the covered entity’s personnel, assets, and nonpublic information in the event of an emergency or other disruption of normal business activities. This Plan must:
- identify documents, data, facilities, infrastructure, personnel, and competencies essential to the continued operations of the entity’s business;
- Identify supervisory personnel responsible for implementing each aspect of the BCDR Plan;
- Include a communication plan for essential personnel;
- Include procedures for the maintenance of backup facilities, systems, and infrastructure, alternate staffing, and the recovery of data and documentation to resume normal operations;
- Include procedures for backup and copying documents and essential data; and
- Identify necessary third parties for continued operations of the cover entity’s business.
Risk Assessment and Management
The draft amendments build on the existing risk assessment and management requirements to ensure cyber risk is adequately and independently identified by qualified personnel or a more defined schedule. These adjustments increase the scope and frequency of risk assessment and ensure that assessors have the independence and information necessary to identify and document cyber risk.
Expanded scope of risk assessment definition (§500.1(n))
The draft amendments expand the definition and scope of risk assessments to include the process of identifying cybersecurity risks to operations, assets, individuals, customers, consumers, third parties, and critical infrastructure, based on the characteristics of the entity, and how identified risks are mitigated.
Expanded scope of penetration testing by independent parties (§500.1(j))
Penetration testing must now be done from both inside and outside the information system’s boundaries and by a qualified internal or external party at least annually. This expands the scope and standardizes the frequency of penetration testing which was previously based on the assessed risk of the information system.
Increased access management requirements (§500.7(a))
Part 500 currently requires covered entities to restrict access to information systems with nonpublic information and conduct a periodical review of privileged access. The draft amendments expand these requirements to ensure privileged access is limited both in number and use, access privileges are reviewed at least annually, remote control protocols are disabled or securely configured, and access is terminated following departure from the covered entity.
More frequent risk assessments (§500.9(c))
Under the draft amendments, risk assessments must be updated at least annually. Additionally, risk assessments must be conducted whenever a change in the business or technology causes a material change to the covered entity’s cybersecurity risk.
Vulnerability scans (§500.5(a)(2))
Covered entities will be required to conduct systematic vulnerability scans on all information systems with a frequency determined by the assessed risk of the information system.
Modified multi-factor authentication obligations (§500.12(b))
The current provisions of Part 500 require covered entities to utilize multi-factor authentication when appropriate based on assessed risks and when any individual is accessing a covered entity’s internal network from an external network unless the CISO has approved compensating controls. The draft amendments modify this requirement and require multi-factor authentication to be used for all privileged accounts and remote access to the network and enterprise and third-party applications from which nonpublic information is accessible.
New requirements for an asset inventory (§500.13(a))
Covered entities shall implement the necessary policies and procedures to document an asset inventory, including tracking information for each asset and the frequency required to update and validate the covered entity’s asset inventory.
Cybersecurity Safeguards
The draft amendments require covered entities to implement additional safeguards and regularly review the safeguards that have been implemented for feasibility and efficacy.
New email and web traffic filtering requirements (§500.14(a)(2))
Under the draft amendments, covered entities will be required to monitor and filter web traffic and emails to block malicious content from reaching authorized users.
Additional encryption requirements (§500.15(a))
In addition to the existing encryption requirements of Part 500, the draft amendments will require a written encryption policy that meets industry standards and at least an annual review of the feasibility of encryption and the effectiveness of any compensating controls.
Notification Requirements
Under the draft amendments, written notice would provide substantially more transparency into the cybersecurity posture of the covered entity. To accomplish this, the amendments define particular deadlines by which notice must be provided, provide an opportunity for entities to acknowledge noncompliance, and require notice when making payments as a result of extortion.
Increased notification superintendent requirements (§500.17(a))
Existing notification requirements have been expanded under the draft amendments to require the notification of the superintendent within 72 hours of a cybersecurity event where an unauthorized user has gained access to a privileged account or an event that resulted in the deployment of ransomware within a material part of the covered entity’s information system.
Additional notice of compliance requirements and introduction of written acknowledgments (§500.17(b))
Under the draft amendments, covered entities must file a notice of compliance, by April 15, based on data and documentation sufficiently accurate to determine and demonstrate full compliance. Additionally, the draft amendments introduce written acknowledgments, within which covered entities who fail to fully comply with the requirements of Part 500 acknowledge this lack of compliance, identify the provisions with which they are not in compliance, identify all areas, systems, and processes that require material improvement, updating, or redesign, and provide a remediation plan and timeline for their implementation.
New notice requirement for extortion payments (§500.17(c))
The draft amendments create a new obligation for covered entities to provide notice and explanation of extortion payment in the event of a payment made in connection with a cybersecurity event. The notice of payment must be filed within 24 hours of payment followed by a written description of the reasons payment was necessary within 30 days of payment.
Violation Threshold and Mitigating Factors
The draft amendments provide a strict one-strike violation policy, but also introduce an extended set of mitigation factors on which NYDFS may rely when evaluating the violation.
New threshold for violations (§500.20(b))
Under the draft amendments, a single prohibited act or failure to satisfy an obligation constitutes a violation.
Expansion of mitigating factors for violations (§500.20(c))
In addition to a clarified threshold for violations, the draft amendments extend the mitigating factors currently provided in the Banking Law to other NYDFS-regulated entities, including those covered by the Insurance Law and Financial Services Law. These factors allow for NYDFS to consider such characteristics as the entity’s compliance history, demonstrated good faith efforts, and the extent of harm caused by the noncompliance and include:
- The extent to which the covered entity has cooperated with the superintendent in the investigation of such acts;
- The good faith of the entity;
- Whether the violations resulted from conduct that was unintentional or inadvertent, reckless, or intentional and deliberate;
- Whether the violation was a result of failure to remedy previous examination matters requiring attention or failing to adhere to any disciplinary letter, letter of instructions or similar;
- Any history of prior violations;
- Whether the violation involved an isolated incident, repeat violations, systemic violations, or a pattern of violations;
- Whether the covered entity provided false or misleading information;
- The extent of harm to consumers;
- Whether required, accurate and timely disclosures were made to affected consumers;
- The gravity of the violations;
- The number of violations and the length of time over which they occurred;
- The extent, if any, to which the senior governing body participated therein;
- Any penalty or sanction imposed by any other regulatory agency;
- The financial resources, net worth, and annual business volume of the covered entity and its affiliates; and
- Such other matters as justice and the public interest require.
How We Can Help
With deep expertise and strategic partnerships with top technology providers, our risk, compliance, cybersecurity, and data protection teams are ready to establish the governance structures and internal culture necessary for NYCRR 500 compliance.
To get help today, contact Biovell .
